Secure Web Access
Contents
Introduction
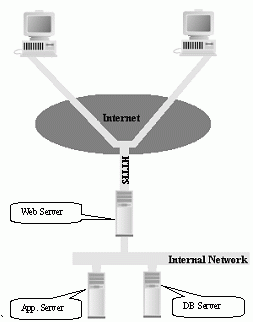
In a secure web access scenario, users connect to a web server with HTTPS enabled which forwards packets to an application server while the application server interacts with a database server which is configured to accept incoming connections only from the application server.
In this model, when the HTTPS connection is setup between the client machine and the web server, all communications are encrypted which guarantees the information security to some reasonable extent.
Server Configuration Guidelines
It is recommended that you use 3 separate machines for improved security:
- Web server
- Application server
- Database server
Also it’s recommended to use an OS which provides you with strict access control over the files and ports, such as FreeBSD.
Web Server
In this model, web server acts as the information gate, so secure it as much as possible.
- Configure a firewall on the web server in a way that all ports on the machine except port 80 -to allow web access- are closed. Note that the firewall can be a separate machine acting only as a packet forwarder to the web server.
- Enable HTTPS on the web server.
- Configure the web server so that it forwards communications on port 80 to the application server –this may be another port on the application server e.g. 8099.
Example:
Web server: Apache with mod_ssl enabled and configured to forward connections on port 80 to port 8099 on the application server.
Firewall: Berkley PacketFilter aka pf or bpf
Application Server
In this model, application server only responds to connections from the web server.
- Configure a firewall on the application server in a way that all ports on the machine except port 80 or whatever port you choose -to allow communication with web server- and database port -to allow communication with database server-are closed.
- Setup the application server so that it only accepts connections from the web server.
Database Server
In this model, database server only responds to connections from the application server.
- Configure a firewall on the database server in a way that all ports on the machine except one port -to allow communication with application server- are closed. For example on a PostgreSQL server the port could be 5432.
- Setup the database server so that it only accepts connections from the application server.
Further Recommendations
- HTTPS is prone to man-in-the-middle attack. A good solution would be configuring SSL in a way that users have to decrypt the key using their passphrase prior to initiating the HTTPS connection.
- As it’s possible for the intruder to take control of the web server machine, it’s strongly recommended to use a UNIX-like OS on that machine, as it prevents the ‘www’ user –the intruder- from accessing files/ports.
- When configuring application and database server, it’s a good idea to use ports other than the common ones –example would be 32320 for PostgreSQL and 7624 for application server ; this has little overall effect but makes gaining control of the machines harder for the intruder.
- The connections between web, application and database server can be configured to be tunneled through SSH providing increased security and authentication.
Caveat Emptor
- HTTPS is prone to XSS attacks. While this kind of attack is not likely to happen on a private application like ADempiere, it has its own risks.